Computer networks are the foundation upon which much of society’s commerce and communication are built. Without networks there would be no Internet and social media would be non-existent. The benefits of the connectivity that networks provide cannot be disputed. However, the advantages that networks offer do not come without a price. In order to safely make use of these complex systems, the concept of network security must be understood and implemented by those in charge of maintaining the infrastructure that they are built upon.
What is Network Security?
Broadly defined, network security is comprised of processes that protect the network infrastructure from the dangers of unauthorized access, misuse, or destruction. It makes use of hardware and software techniques in an effort to create a secure environment from which users and programs can perform their functions safely. There are three main components to robust network security which are:
Protection – Networks should be configured in a way that emphasizes their security. A well-configured network will be harder for unauthorized users to crack.
Detection – The timely detection of configuration changes, network traffic issues, or unauthorized access is critical to maintaining a secure system.
Reaction – In the event that problems do arise, you need to ability to address them quickly.
There are many tools and methods that are employed to enhance network security. They include:
- Firewalls – A firewall is one of the basic forms of protection which controls the flow of traffic between your network or computer and the Internet. It allows you to define rules that limit access to your network.
- Anti-malware software – Another layer of protection for your network and its attached devices is the inclusion of high quality anti-malware and anti-virus protection. The goal is to prevent the introduction of malicious code into your environment and quickly identify and eradicate it if it does slip through the initial line of defense.
- Access control – Only authorized users should have access to your network and they should be restricted to using the resources to which they were specifically assigned.
- Intrusion detection and prevention – These tools attempt to identify and block attacks before they can affect your system.
- Behavioral analytics – Understanding the characteristics of normal network behavior for your environment allows you to detect suspicious patterns or activity that may indicate a security breach.
- Email security – Tools that enforce email security can minimize the risk of your users being exposed to phishing attacks and prevent them from sending confidential data out of the network.
- VPN – A virtual private network creates an encrypted tunnel through which your network data transmission can travel securely.
These methods of enhancing network security are applicable to both wired and wireless networks. In addition to the general procedures required to secure any network, wireless and WiFi networks introduce other factors that can impact the safety and privacy of their users.
Wireless network security
The very nature of a wireless network makes it more susceptible to attacks and attempts to gain unauthorized access. Wireless signals from the network router can be accessed by anyone within range. They could conceivably be located outside your building and be conducting attacks undetected, which is not an issue with wired networks requiring physical access. This introduces further security concerns and demands further precautions to protect a wireless network.
Some of the additional steps required to secure a wireless network include:
Change default passwords – Change the default password on all routers and access points to a strong password to ensure their security.
Encrypt network data – Configure your router and network to use the strongest encryption available. At a minimum, you want to use WPA2 level encryption combined with a strong network password to protect the network’s valuable data.
Control network access – Signal leakage outside of your intended coverage area can lead to rogue access points that can be used by malicious intruders. Managing your wireless signal to provide adequate coverage to your users while inhibiting unauthorized access can be challenging and demands the use of specialized WiFi monitoring tools.
Network security tools
Wireless Network Defensive Tools
Defending a wireless network from attacks by unauthorized users often demands taking preventative measures to thwart their efforts. In many cases, the same tools used by hackers to attempt to subvert your security can be employed to strengthen the safety of your network.
Subjecting your network to an investigation and attempting to crack it will necessitate the use of the same tools that malicious intruders will be wielding. They will allow you to test the strength of your network security and identify flaws that need to be addressed. If you can break into your own network, rest assured, so can the hackers. Here are some tools that can help in that effort.
KisMac2 is an open-source, wireless network discovery tool developed for the Mac OS X operating system. It is a powerful app that can be used to crack WEP and WPA keys using brute force attacks and packet re-injection.
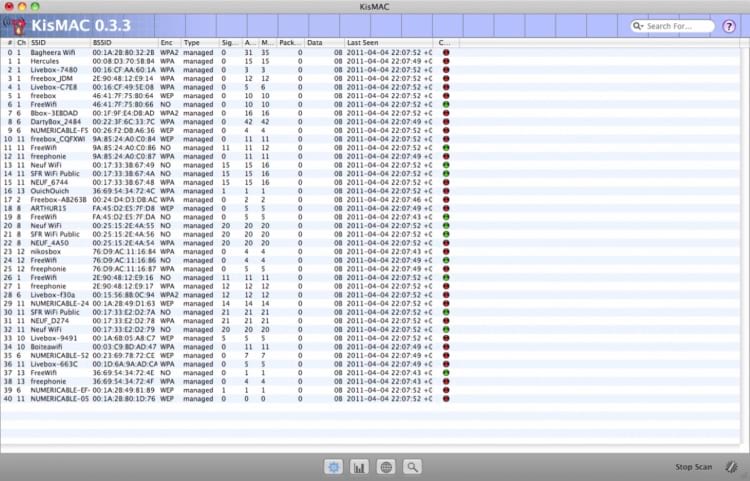
It can scan for networks in active or passive mode and can be helpful in identifying weaknesses in your WiFi network.
Aircrack enables you to identify weak points in your wireless network’s security. You can attempt to crack your encryption password and test the capabilities of your WiFi cards and drivers.
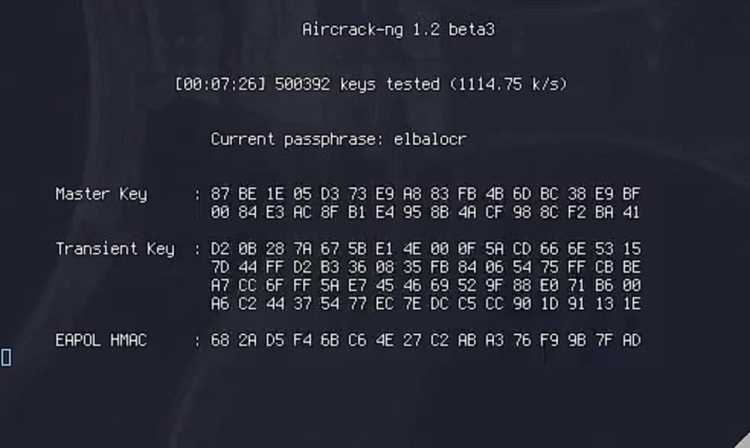
Replay attacks on your network and export packet data to text files for later analysis. It’s a versatile tool that can help prevent rogue access to your wireless network.
NetStumbler is a WiFi stumbler for Windows computers. It automatically scans for wireless networks as soon as launched and supports many available network cards. The free utility has an interface which is reminiscent of Windows Explorer making it easy to navigate.
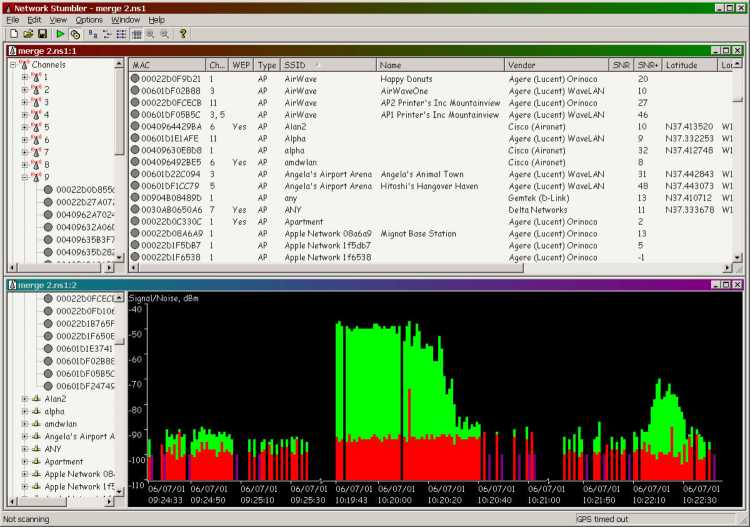
It can help you find rogue access points and coverage issues with your WiFi network that need to be addressed to enhance security.
Packet Sniffers
Packet sniffers or analyzers are tools that capture data packets transmitted by a network. Once the data is captured, the software analyzes it and renders it into some type of human-readable format. These captured packets can contain sensitive data including login information, passwords, and financial details that you do not want to be made available to the public. Using a packet sniffer on your network can alert you to changes that need to be made in your encryption or security policies.
Wireshark is a very popular free and open-source network packet analyzer. It runs on Linux, macOS, and Windows, providing the user with the ability to browse data in a GUI or the TTY-mode TShark utility.

The software is supported by an extensive user community and there are many online resources available to streamline your use of the tool.
KisMac2 can also be used for packet sniffing and injection testing, making it a versatile tool for macOS users with wireless networks.

Collect packets from your network to see if you are accidentally exposing your data to unauthorized use.
Steel Central Packet Analyzer offers an enterprise-grade network packet sniffer that is suitable for small and large companies. It has an intuitive user interface that incorporates graphical representations of your network data for easier analysis.
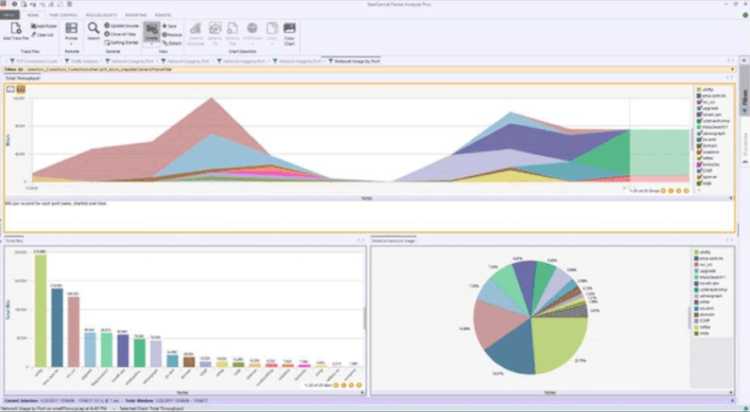
The tool can be configured to alert you of abnormal network behavior. Drill down in the user interface to quickly find the exact cause of network issues.
Network Security Monitoring Tools
Monitoring your network can be done in a variety of ways. You may employ software that monitors traffic in real-time and alerts you to potential threats posed by unauthorized access. Gathering network statistics over extended periods of time can be useful for security analysis and strengthening weak points. Wireless networks pose the additional problem of signal leakage that can be addressed by testing and monitoring. Here are a few tools which can be used to monitor your network in an effort to bolster its security.
NetSpot enables users to create heat maps of their network’s WiFi strength and test the signal from any location. This facility lets you identify rogue access points that may be outside of your building. These can pose significant risks to your network and should be addressed and minimized if at all possible.

Periodically surveying your wireless network in this manner can help protect it from malicious intrusions. This software is available in a free version and runs on most computing platforms.
Solarwinds Network Performance Monitor is a solution intended for use on large, mission-critical networks. The tool offers advanced network and device monitoring that can be instrumental in fully securing your network.
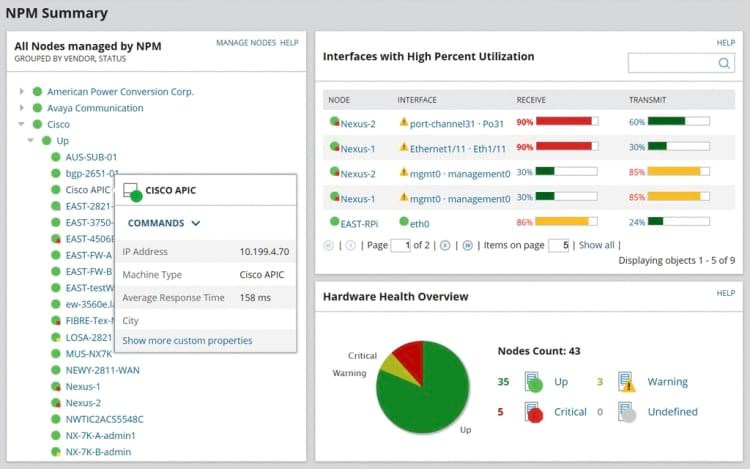
Create custom alerts and allow the software to automatically generate maps of network devices for your analysis. It’s a flexible and scalable monitoring package designed to enhance your network’s security and performance.
Nagios is another network monitoring tool that is suitable for implementation in large corporate networks as well as smaller installations. Flexible alerting and logging are two of the outstanding features of this software package.
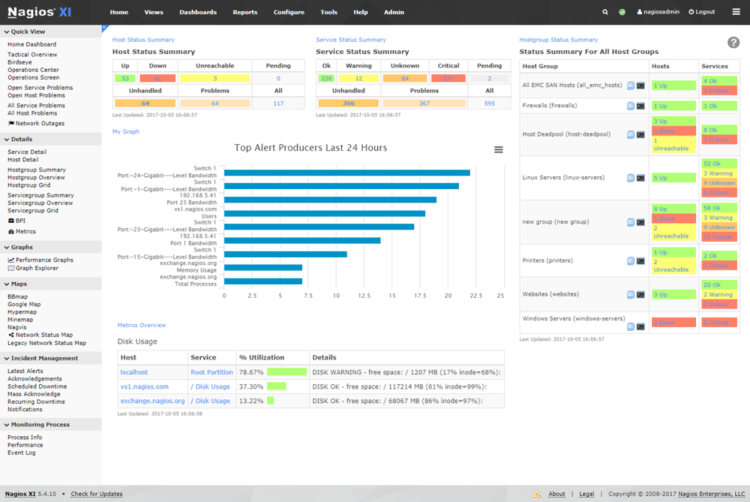
Perform bandwidth, SNMP, switch, and overall network monitoring to obtain a clear picture of your system’s performance and vulnerabilities.
Securing your network is a critical step in maintaining the privacy and confidentiality of your users and their data. Failure to implement network security leaves you open to attacks and unauthorized access which compromise the safety of your systems and users.