In cases where sensitive data is being transferred across a wireless connection, the security of the network is critically important. Many tools and methods can be employed to protect the safety of wireless networks. One method that can be conducted by security professionals, as well as home users, is penetration testing.
What is Penetration Testing?
Network penetration testing is the process through which a network is tested to proactively identify security weaknesses. The goal is to find weak spots in your network security before it is breached by unauthorized users. This could involve finding problems affecting a number of aspects of your wireless network.
Before conducting penetration testing you need to gather some information regarding the network to be tested. This includes:
- Creating a heat map of the area to detect the range and footprint of the wireless signal.
- Identifying the number of SSIDs.
- Inventorying the hardware involved in the wireless network configuration.
You also need to consider the type of threats you are likely to encounter. The type and scope of probable attacks can be deduced from certain details about your network. Some examples are:
- Based on the area in which the WiFi signal is detected, you can determine whether potential attacks can come from outside the building or if they would need to be launched within your home or office.
- The type of hardware used to implement the network can impact the type of attacks from which you are most vulnerable.
- The type of equipment that can be accessed through the network plays a part in the probability of experiencing an attack. Hackers are more likely to try to gain access if the intrusion leads to accessible file servers or multiple workstations.
Armed with the knowledge gained from the previous steps, you can more effectively engage in penetration testing.
Why Should You Perform Penetration Testing?
You should perform penetration testing to verify the security of your home or business wireless network. The testing can be instrumental in keeping the network and its associated machines and data secure. The purpose of the tests is to find areas where your network might be susceptible to attack by hackers.
Addressing these problems before they are exploited can potentially save you a lot of time and money. Failure to do so puts your sensitive information at risk. Think about the kind of information you transmit wirelessly and the ramifications of that data landing in the wrong hands.
Even if the previous testing showed no areas of concern, routinely performing a penetration test should be strongly considered if you value the security of your wireless network. It should be periodically scheduled if your network configuration remains stable. You should certainly perform additional tests if your network changes or expands by the addition of new devices or access points.
What Types of Attacks are Common?
There are many types of attacks which can be carried out by hackers on wireless networks. The goal of these attacks is essentially the same. They are intended to allow unauthorized access to the network and potentially the connected devices. Let’s look at some of the most commonly used methods of attack that may impact your network.
Packet injection or reinjection – This is a very common method of hackers attempting to gain access to a wireless network. Packet injection allows the hacker to spoof a computer’s credentials and direct network traffic to their machine.
Packet sniffing – Here, a malicious individual monitors networks in the hopes of encountering unencrypted data. This highlights the need to enforce security on your network and encrypt data transmission with a VPN.
Password cracking – Just as its name infers, this is the process of attempting to find the password of a protected network. Also referred to as an encryption attack, a hacker can try to do this in a number of ways including:
- Brute force attacks in which an application generates random sequences of characters, perhaps regulated by some parameters, to query the password. This is a time and processor-intensive activity.
- Wordlist attacks are similar to brute force attacks except that they make use of a dictionary file which contains the words or character sequences that will be tested against the network’s password. The success of this type of attack is usually tied to the size and quality of the dictionary file.
Evil twins and fake access points – Public WiFi installations are especially prone to these types of attacks. Hackers set up fake access points that induce a user to believe they are connecting to a valid network. Once connected, the user’s data is accessible to the hacker.
The quality of the encryption method you employ has a direct impact on the potential that the password will be cracked. We will see this in action when we look at how to actually perform penetration testing.
How to Perform Penetration Testing on macOS (OS X) with KisMAC
Network penetration testing tools are required in order to perform a penetration test. KisMAC is a free network analyzer that can serve as a tool with which to perform penetration testing. This freeware was developed to run on the macOS and supports a wide range of WiFi cards. It just also happens to be a great tool for performing attacks on wireless networks. This aspect of the app makes it perfect for penetration testing. You can use the program to attempt to subvert your own network security.
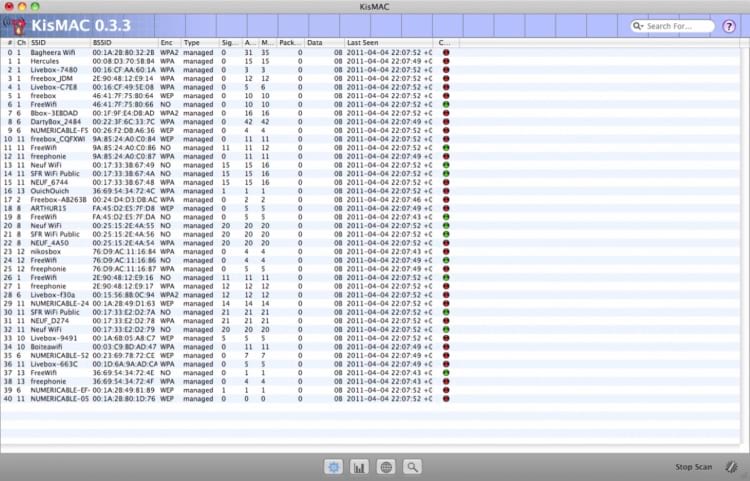
Let’s take a look at how to perform some penetration testing using this application. You want to download and install the program on a MacBook so you can freely move beyond the coverage area to conduct your tests.
Once the program is installed, fire it up and scan for networks. You can use this opportunity to take the application for a walk and see where the signal can be accessed. This information can help you identify potential areas to monitor for rogue access attempts such as those from a parked car.
The most basic form of encryption in general use is the Wired Equivalent Privacy (WEP) standard. If your network uses this form of encryption, you might consider upgrading to a more secure method. Here’s how to use KisMAC to try to crack a WEP protected network.
KisMAC has three methods of WEP cracking built into the app. It can conduct wordlist, brute force, and weak scheduling attacks. Two hosts are required to conduct the attack. One will be used to inject traffic while the other captures traffic, specifically initialization vectors (IVs).
In KisMAC’s network menu, you can drill down and select the Crack option which opens a sub-menu, enabling you to choose the type of cracking you want to employ. If you have the time, chances are good that you can gain access to a WEP protected network using this application.
WiFi Protected Access (WPA) is a stronger encryption method that can also be tested with KisMAC. You will only be successful in cracking a WPA protected network if a short password or passphrase is used. This type of attack is conducted offline with a dictionary file which must contain the correct password. Essentially, you steal a WPA pre-shared key and attempt to crack it at a later time.
KisMAC can also be used to perform wordlist attacks on other encryption methods including 40 and 104 bit Apple keys and Cisco’s LEAP keys.
While penetration testing in itself will not fully protect your wireless network, it can indicate steps that need to be taken to increase its security. Making use of penetration testing tools such as KisMAC should be part of your overall network security protocol.